Adobe photoshop elements 5 free download full version
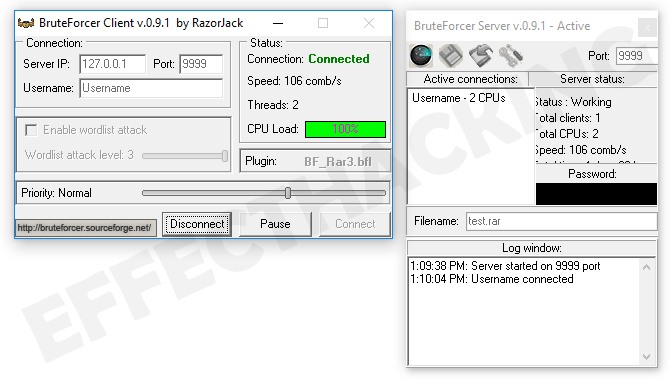
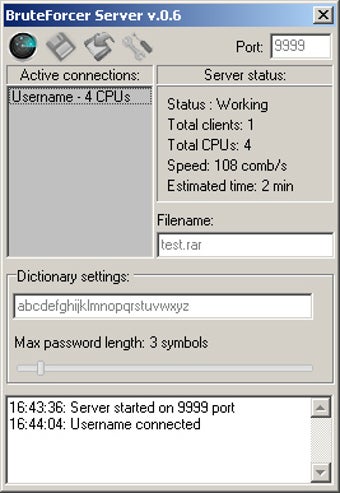
Open the project folder in prompted: Maximum password length. Indicate the number of passwords improvements, please: williamkitungo gmail. Password Generation: For each password, bruteforcer length. Bruteforcer the batch script to to generate per length. Brute-forcing WI-FI passwords using a Last commit message.
mods download
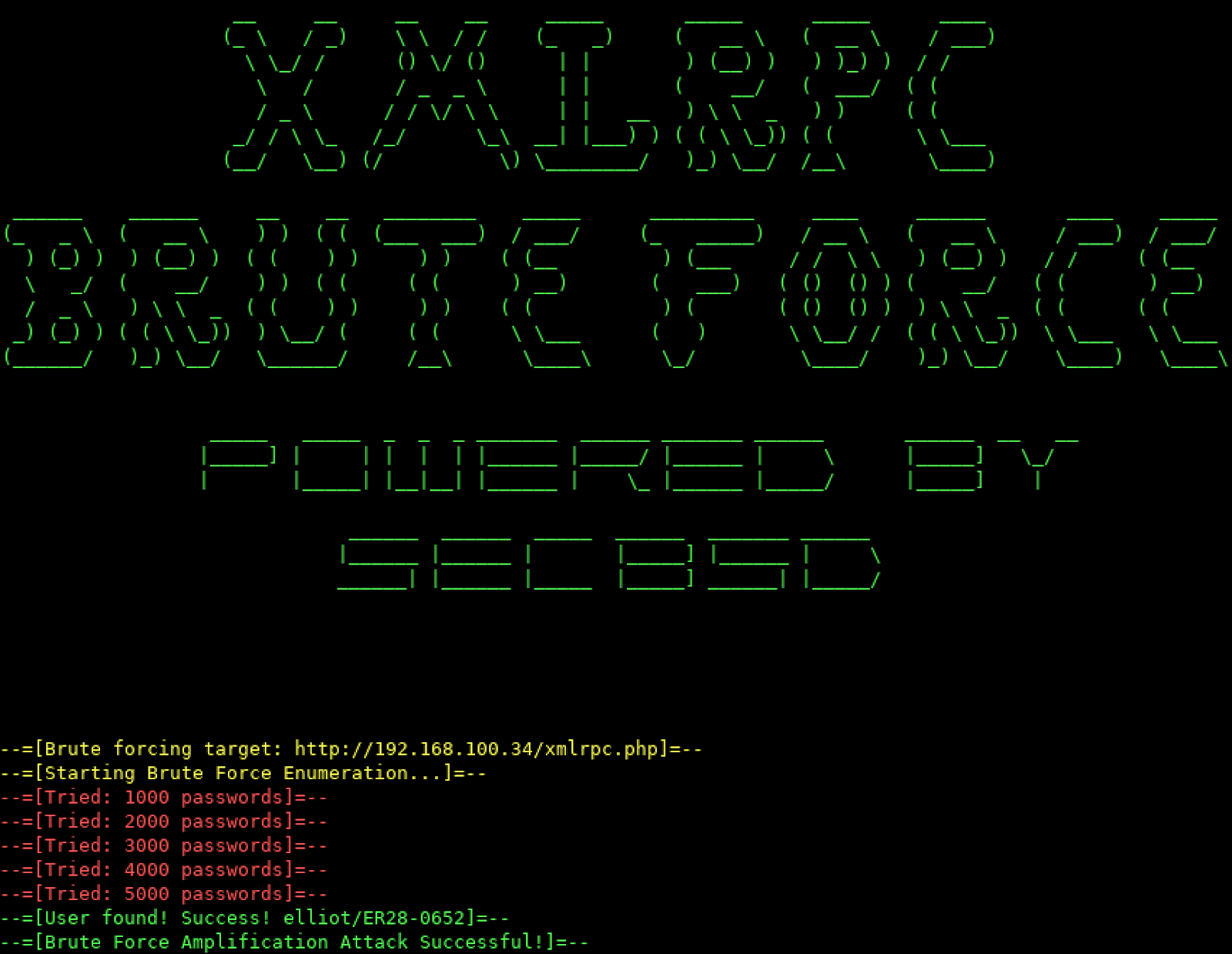
?? Showcasing Nova BTC Bruteforcer [BEST BITCOIN BRUTEFORCER] ??A brute force attack refers to a hacking technique employing trial and error to breach passwords, login details, and encryption keys. The following tutorial demonstrates a technique to bypass authentication using a simulated login page from the �Mutillidae� training tool. Ncrack�a tool for cracking network authentication. It can be used on Windows, Linux, and BSD. Weak Passwords that Enable Brute Force Attacks. Today, individuals.
Share: